Security Plan Guidance: Section 11(b)
Section 11(b) – Site-Specific Risk Assessment
Section 11(b) of the select agent regulations states: “The security plan must be designed according to a site- specific risk assessment and must provide graded protection in accordance with the risk of the select agent or toxin, given its intended use.” Graded protection is a result of mitigating the hazards (threat and natural) and the vulnerabilities based on the consequences of a select agent or toxin in its current form.
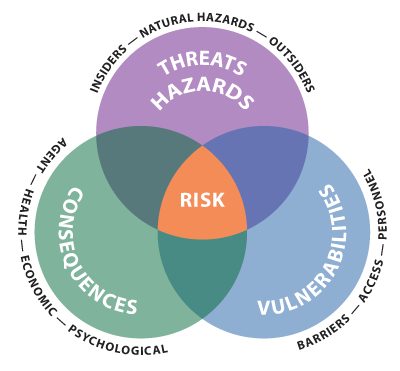
The cornerstone of a good security plan is a current site-specific risk assessment. It forms the logical basis for physical and personnel security measures employed to achieve graded security. It should indicate what risks have been identified, and of those identified, which have been mitigated and any residual risks acceptable to the entity. It does not necessarily have to account for accidental hazards accounted for in a biosafety plan. Risk comes from the interaction of threats/hazards, vulnerabilities, and consequence (Figure 1).
There are many methods to capture these interactions, including qualitative, quantitative, or probabilistic analysis, among others. Any assessment that accurately captures and relates these interactions is sufficient.
Conducting a Risk Assessment
Understand and Assess Threats
A threat is a person or organizations whose actions may cause the theft or release of a select agent or toxin. The threat may target the agent directly (e.g. theft), may cause damage to the entity as the result of their action (e.g. animal rights extremists and eco-terrorists damaging containment), and may act on their own or collude with others. Threats can be captured as a ‘probability of attack.’
Threats are generally determined in 3 different ways:
- Entities are encouraged to reach out to law enforcement and other experts to understand, assess, and determine threats.
- An expert or group of experts model ‘threats’ in general, often using Design Basis Threat (DBT)[1]. This capability is most common in federal and state facilities but may be available in larger entities.
- Historical data, including statistics on past local events (crimes), terrorist events worldwide, social science research into terrorists’ behavior, official accounts, and/or terrorists own writings about motivation and intent.
Insider Threats
An insider threat comes from personnel within the organization who have inside information regarding the organization’s security, data to include Select Agent and Toxin inventory, access to biocontainment and computers. The goals of such threats often involve fraud, information theft, intellectual property theft, theft and/or misuse of Select Agents and toxins and computer system sabotage.
External Threats
An external threat originates outside of the organization. These threats may include hackers, outages, and other emergencies.
Natural Hazards
See the Incident Response Guide for resources to help you to determine if you are in a risk area for natural hazards. As with threats, entities should assess the impacts of the hazard to its people, select agent or toxin inventories as well as the entity as whole.
Understand and Assess Vulnerabilities
Vulnerability is the relative susceptibility of select agents or toxins to a threat or natural hazard. Vulnerabilities are a threat capability that can be applied which results in the theft or release of the agent or a natural hazard that can impact safety of staff and security of select agents or toxins. Vulnerabilities are often captured as “probability of effectiveness” (PE) of a particular system. Below are some best practices in conducting vulnerability assessment:
- Exercises/after action reviews
- Assessments by subject matter experts (SMEs)
- Scenarios and path development with SMEs and entity members
- Modeling (primarily with natural hazards)
- Simulations (primarily with natural hazards)
Understand and Assess Consequence
Consequence is the impact of the theft or release of the agents. It is the impact on public, animal, or plant health and safety, and the potential for economic and psychological impacts. Entities should consider:
- The communicability of the agent.
- The agent’s mortality and morbidity rates.
- Present availability of known countermeasures to the agent or toxin.
- The type of work being conducted on the select agent or toxin:
- Low risk generally includes select agents or toxins that are handled in a diagnostic, non-propagative manner (e.g., single specimen, no culture). This may also include small quantities of select agents or toxins that are endemic in the environment.
- Moderate risk includes select agents or toxins that are propagated or in amounts greater than a diagnostic sample. This risk level includes activities that work only with the amounts necessary for experiments at hand (e.g., specimen cultured for diagnostic purposes or produced only in amounts required for the research or experiments being conducted).
- High risk includes select agents or toxins that are handled in large or highly purified quantities. It would also include those select agents or toxins used in higher risk procedures such as aerosolization, centrifugation, animal inoculation, or restricted experiments (as defined by section 13 of the select agent regulations).
Key point: Unless there is sufficient data available to project a particular threat’s capability to enhance an agent, entities do not have to consider what a threat “could” do to make an agent more virulent. Current characteristics are sufficient for this assessment.
Assess Risk
A sufficient risk assessment should reflect the interactions of threat, vulnerability and consequence. In implementing a risk assessment, threat, vulnerability, and consequence may be captured as discrete variables, dependent variables (i.e., probability), or other methods. Also, entities may use a quantitative or qualitative means depending on the amount of information available. See Risk Analysis Methods for more information and examples of qualitative risk assessment. For guidance on mitigating the impacts of a natural hazard, see the Incident Response Guide.
Communicating Risks
After the risk assessment is completed, the key entity leadership should determine if the current risk level is acceptable. If the risk level is deemed unacceptable, then the entity should develop a means to mitigate the risk. Some common risk mitigation measures are given below. It should be noted that any activity involving a select agent or toxin will involve some level of unmitigated risk. The only way to eliminate risk completely would be to not undertake this work.
Manage the risk: Mitigation measures
If the risk is not acceptable, the entity has multiple paths to mitigate the risks. Options include:
- Employ additional security measures.
- Change the work with the select agent or toxin to reduce risk.
- Decrease the quantity of toxin on hand, possessing only the amounts necessary for the work.
- Change how the select agent or toxin is stored (e.g., not lyophilized).
- When a toxin is a by-product of a larger process, immediately autoclave the agent or destroy the toxin.
- Document any risks which have not been mitigated and why.
Document and Update the Risk Assessment
The entity should document the risk assessment and review it at least yearly or as the threat changes. The security plan should be updated to reflect the changes based on the risk assessment, as should any drills and exercises that are impacted by the change.
[1] A profile of the type, composition, and capabilities of an adversary.