Security Plan Guidance:
Section 11(f) – Tier 1 Security
Section 11(f) – Tier 1 Security
Tier 1 select agents and toxins require additional security measures to be implemented including the addition of pre-access suitability assessments, extra access controls, and extra barriers. These extra measures are intended to safeguard Tier 1 select agents and toxins further from theft, loss, or release. The list of Tier 1 select agents and toxins includes:
- Bacillus anthracis
- Bacillus cereus Biovar anthracis
- Botulinum neurotoxins
- Botulinum neurotoxin producing species of Clostridium
- Burkholderia mallei
- Burkholderia pseudomallei
- Ebolavirus
- Foot-and-mouth disease virus
- Francisella tularensis
- Marburg virus
- Rinderpest virus
- Variola major virus (Smallpox virus)
- Variola minor virus (Alastrim)
- Yersinia pestis
An effective security plan for Tier 1 BSAT describes how the requirements of the regulations are met. The security plan should also discuss who manages security control measures. This may include:
- How the entity manages access controls – This management may include keys, card keys, access logs, biometrics and other access control measures for each of the security barriers in the security plan. This may be accomplished by directly controlling or interacting with a service provider (e.g., a security guard company).
- Designating personnel to manage the entity’s security systems, including intrusion detection
- How the intrusion detection alarm code is managed (who has it, when it is changed)
- How the entity tests and manages the configuration of the system
- How the entity responds to an access control or intrusion detection failure (e.g., alarm)
- How the entity screens visitors
Section 11(f)(1) – Pre-Access Suitability Assessment
The entity must develop, implement, and describe in the security plan procedures for conducting a pre-access suitability assessment of persons who will have access to a Tier 1 select agent or toxin. See the Guidance on Suitability Assessments. Individuals must have a pre-access suitability assessment conducted before they are allowed access to Tier 1 select agents and toxins.
Section 11(f)(2) – Responsible Official Coordination with Other Safety and Security Professionals
Entities must describe procedures for how an entity’s Responsible Official (RO) will coordinate their efforts with the entity’s safety and security professionals to ensure security of Tier 1 select agents and toxins and share, as appropriate.
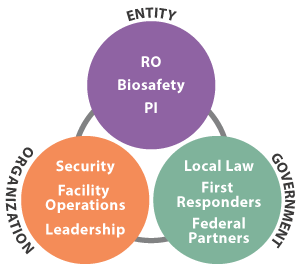
Ideally the entity’s RO, safety, and security professionals should meet on a regular or defined basis. This may be annually in conjunction with the security plan review, after a security incident, when there is a significant entity change that affects security, or in response to a threat. See Figure 1 for an example of the personnel who should be involved in creating a security plan for entities registered to possess or use Tier 1 BSAT.
Section 11(f)(3) – Ongoing Suitability Assessments
Describe procedures for the ongoing assessment of the suitability of personnel with access to a Tier 1 select agent or toxin. See the Guidance on Suitability Assessments. The procedures must include:
- Self-Reporting – Individuals should be trained on how to report any incidents or conditions that might impact their ability to safely have access to select agents and toxins and to safeguard them from theft, loss, or release.
- Peer-Reporting – Individuals should be trained on how to report incidents or conditions that might impact the ability of others to safely have access to select agents and toxins. Peer-reporting should be safe and anonymous and protect whistle-blowers from repercussion.
- Employee Training – All employees must be trained on the entity’s policies and procedures for reporting, evaluating, and corrective actions concerning suitability assessments. This type of training may include threat awareness, self- and peer-reporting, behaviors of concern, and suitability policies.
- Ongoing Suitability Monitoring – All individuals with access to Tier 1 select agents and toxins must undergo ongoing suitability monitoring. There are several ways to achieve this, including annual performance reviews, access reviews, and criminal record reviews.
Section 11(f)(4) – Security Enhancements
Entities that possess Tier 1 select agents and toxins must adhere to extra security enhancements, including access limitations, extra barriers, intrusion detection system, and visitation policies.
Section 11(f)(4)(i) requires the entity to limit access to a Tier 1 select agent or toxin to only personnel who have been approved by the HHS Secretary or APHIS Administrator, following a security risk assessment (SRA) conducted by the Attorney General, and have had an entity-conducted pre-access suitability assessment. Such individuals must also be enrolled in an ongoing suitability assessment program conducted by the entity.
- Make sure that only HHS or USDA approved individuals have access to Tier 1 BSAT.
- Conduct a pre-access suitability assessment before granting access.
- Enroll each individual to be given access to Tier 1 BSAT in an ongoing suitability assessment program
Access Outside Normal Business Hours
Section 11(f)(4)(ii) requires the entity to limit access to registered spaces outside of normal business hours. Only individuals who have been specifically approved by the RO, or his/her designee, may be allowed to access laboratories or storage facilities containing Tier 1 select agents and toxins outside of normal business hours.
Limit access to registered spaces outside of normal business hours. This does not mean that personnel cannot work outside these hours; however, they should get specific approval by the RO, or his/her designee, before doing so. The entity may choose to establish specific after-hours work policies. For example, the entity could establish a 2-person rule for work conducted after hours. This rule should consider, and implement, any necessary justification for after-hours work, such as 24 hour animal studies.
Security Barriers
Section 11(f)(4)(iv) of the select agent regulations requires a minimum of three security barriers safeguarding Tier 1 select agents and toxins against theft, loss, or release. A barrier is a physical structure designed to prevent unauthorized access. Cameras, security lighting, and IDS are not considered security barriers because, while they may monitor and detect unauthorized access, they cannot, by themselves, prevent access. These security barriers must be identified on the entity’s registration (Sections 5A and 6A of APHIS/CDC Form 1) and described in the security plan.
- Implement a minimum of three physical security barriers to safeguard Tier 1 select agent and toxins against theft, loss, or release.
- Intrusion detection systems do not count because they cannot actually prevent access.
- Identify the security barriers in the entity’s registration and describe them in the security plan.
Examples of Acceptable Security Barrier Implementations
| Ex. | Barrier 1 | Barrier 2 | Barrier 3 (linked to access approval) |
|---|---|---|---|
| 1. | Guard/Perimeter Fence | Card-Key Access to floor | Key locked container with strong key control measures |
| 2. | Building Card Key Access | Limited Room card-key access | Different card-key required for room |
| 3. | Building Card Key Access | Limited Room card-key access | Card-key PIN access room |
| 4. | Building Card Key Access | Limited Room card-key access | Biometric lock system on freezer |
| 5. | Building Card Key Access | Card-key PIN access room | PIN access to freezer |
| 6. | Building Card Key Access | Limited Room card-key access | Restricted card key access to registered space |
| 7. | Floor Card Key Access | Limited Room card-key access | Restricted card key access to registered space |
Security barriers should be implemented based on a site-specific risk assessment and should ensure that the following conditions are met:
- Each security barrier must add to the delay in reaching the areas where select agents and toxins are used or stored. Most security barriers, in and of themselves, do provide additional delay to forced entry.
- All access points, including emergency exits, must be secured. If there is a card key lock on the main door, the emergency exit should be secured to prevent ingress – for example, by having no outside handle.
- One of the security barriers must be monitored in such a way as to detect circumvention of established entry control measures under all conditions. This may include video cameras, monitoring access control logs from a card key reader or other methods of regular monitoring.
- The final security barrier must limit access to the select agents and toxins to personnel approved for access by the HHS Secretary or APHIS Administrator.
- Per section 11(f)(4)(i), the entity must ensure access to the Tier 1 BSAT is limited to those who have undergone the entity’s pre-access suitability and are subject to ongoing suitability assessment. Access records can be used to show that only access approved personnel have accessed the final barrier.
Personnel who are trained to identify and respond to suspicious activities can be a security barrier. Persons who receive ‘insider threat,’ ‘suspicious person’ or similar training along with response procedures (i.e., calling security, 911, etc.) are considered ‘trained personnel.’ Therefore, when they are physically present, they may be considered a security barrier.
Intrusion Detection Systems
Section 11(f)(4)(v) requires the entity to ensure that all registered spaces containing Tier 1 select agents or toxins must be protected by an intrusion detection system (IDS) unless the area is physically occupied. An IDS consists of a sensor device which triggers an alarm when a security breach occurs notifying a response force (e.g., local police, security guard force, etc.) who have the capability to respond to the alarm and stop a threat.
Section 11(f)(4)(vi) requires that personnel monitoring the IDS must be capable of evaluating and interpreting the alarm and alerting the designated security response force or law enforcement. Some response options include:
- Personnel employed by the entity (an alarm or security operations center)
- Contracted alarm company
- Local law enforcement
- Military police unit
- Dedicated entity personnel
If the IDS is monitored by a service provider with a local law enforcement response, the entity should coordinate with local law enforcement to assist them in understanding the importance of the information from the service provider. For example, due to the volume of false alarms, local law enforcement may not treat the alarm as a serious matter. Entities are encouraged to discuss the consequence of theft of a select agent or toxin with local law enforcement so they can appreciate the seriousness of the threat. Local law enforcement should understand that an alarm at an entity housing select agents and toxins should not be regarded as a “typical” property crime.
Intrusion Detection Response Times
Section (11)(f)(4)(viii) requires the entity to determine response times for security forces or the local police to Intrusion Detection Systems. The response time must not exceed 15 minutes from the time that an alarm sounds or a security incident is reported to the arrival of the responders at the first security barrier.
A response force is a force capable of interrupting a threat. It may be unarmed guards, armed guards and/or local law enforcement – though law enforcement is preferable.
The target for response time, 15 minutes or less, is based on the Department of Defense adopted standards for protecting high consequence assets. However, entities are strongly encouraged to coordinate with local law enforcement and/or federal partners to assist with threat assessment to determine the appropriate response time. Local law enforcement, especially in areas where the response time is challenging, will often assist the entity in determining how long the barriers will delay an adversary.
There are many ways to reduce response time for the response force to less than 15 minutes. One method is to perform the following steps:
- Discuss regulatory requirements and strategies with local law enforcement.
- If you have a dedicated guard force, work with them (generally, you will meet this requirement with a dedicated guard force).
- Calculate the delay time provided by entity security barriers and compare it to the expected response time of the response force. Get the typical response times from the responding personnel and compare it to the delay times determined through scenarios.
- Conduct an exercise with local responders.
Though not required, entities should consider the effect of natural hazards when addressing response times.
Access Control Systems
Section (11)(f)(4)(vii) requires the entity to describe procedures to ensure that security is maintained in the event of the failure of access control systems due to power disruption affecting the registered spaces.
In the event of an incident that disrupts or cuts off power to the registered space, the entity must have a plan in place to ensure that security is maintained, and three physical barriers will remain in place, until power can be restored. Some acceptable methods include:
- Failing secure locks that are locked or remain locked when power is interrupted or there is a power outage.
- Adding personnel/guard forces at doors that acts as one of the three physical barriers but may fail open instead of closed/locked in the event of a power failure.
- Backup generators or batteries that will restore power to the access control systems.
For example, if power is lost and the door locks (even if it can be opened only from the inside), then it meets this requirement. If power is lost and door unlocks (it can be open from the outside), then it does not meet “fail secure.”
Depending upon the access control systems (ACS) and equipment, the entity should consider changing lock combinations, ACS password/pin, intrusion detection system (IDS) password/pin, and access approvals in which the departing personnel was assigned when they are removed from the program and/or access to Tier 1 select agents. Former employees that retain the ability to use and control the locks, ACS, and the IDS would pose a vulnerability.
Section 11(f)(5) – Security Enhancements
Entities that possess Variola major virus, Variola minor virus, foot-and-mouth disease virus and rinderpest virus must have additional security requirements as outlined in the select agent regulations.